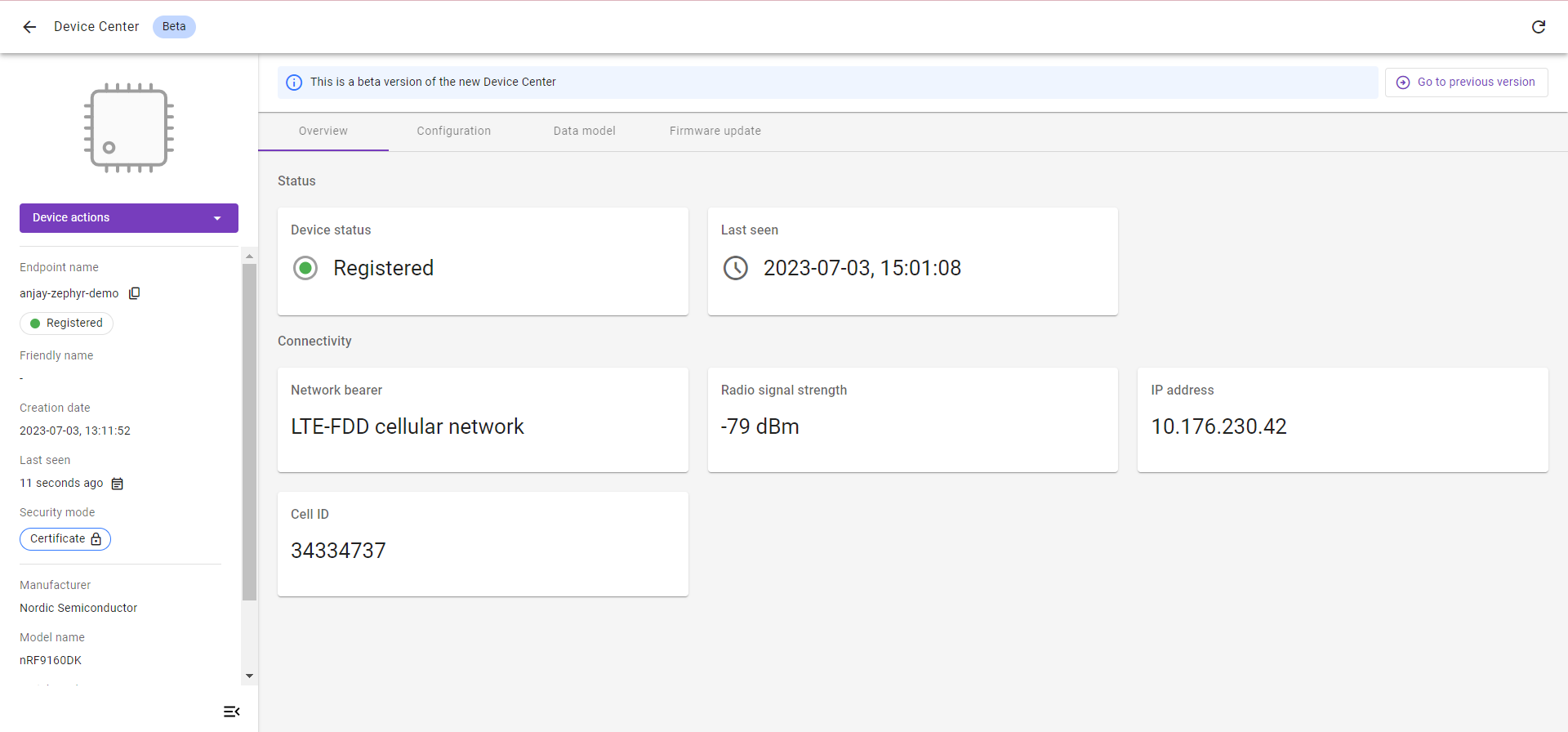
Runtime Certificate and Private Key Configuration#
Introduction#
Anjay library supports secure connection between device and server. Encryption can be achieved with the use of Pre-Shared Key as it was described in nRF9160 DK, nRF7002 DK and Thingy:91 pages or with certificate-based cryptography.
In Certificate Mode an asymmetrical algorithm is used to authenticate the connection endpoints and initialize payload encryption. Appropriate certificates need to be generated for both the LwM2M Client and the LwM2M Server. Public certificates of both parties are mutually available, and each party also has access to its corresponding private key.
You can read more about secure communication on Anjay's documentation page.
Prerequisites#
- The nRF9160 DK board with a USB cable.
- Cloned Anjay-zephyr-client repository
Note
Go through the README's Getting Started part.
- Installed OpenSSL
- Installed minicom (for Linux), RealTerm, PuTTy (for Windows), or another serial communication program.
- An active Coiote IoT DM user account.
Note
The runtime certificate and private key configuration do not work with other boards.
Build and flash the device#
- Connect the nRF9160 DK board to a USB port of your machine.
- Enter the command line interface on your machine and change the directory to the one where you set up the Zephyr project (usually, it's
~/zephyrproject). - Go to your local Anjay-zephyr-client/demo directory
-
Set manifest file to
west-nrf.yml, and dowest update:west config manifest.path Anjay-zephyr-client/demo west config manifest.file west-nrf.yml west update -
Build a project with a runtime certificate and private key.
In order to build application using software cryptography, build using following command:
west build -b nrf9160dk_nrf9160_ns -p -- -DEXTRA_CONF_FILE="overlay_nrf_mbedtls.conf"Note
This feature works with nRF9160 DK starting from revision v0.14.0, which is used by default for
nrf9160dk_nrf9160_nstarget, but you can pass revision explicitly in order to protect against further NCS updates. -
Flash the board with
west flashcommand.
Generate certificate#
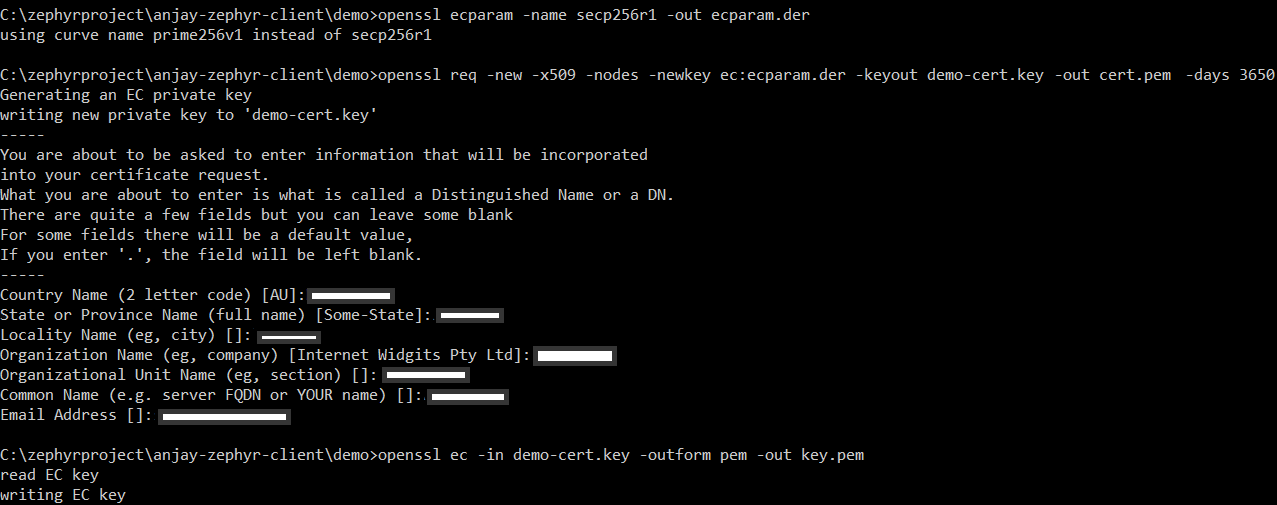
The certificate and private key based on the SECP256R1 curve can be provided through the shell interface in .pem format. To generate To generate a self-signed certificate and key pair open a terminal in the Anjay-zephyr-client/demo directory and use the following commands.
openssl ecparam -name secp256r1 -out ecparam.der
openssl req -new -x509 -nodes -newkey ec:ecparam.der -keyout demo-cert.key -out cert.pem -days 3650
openssl ec -in demo-cert.key -outform pem -out key.pem
Important
To use the certificate and private key with Coiote IoT DM you must specify a common name that is the same as the client endpoint name.
You will see two files cert.pem and key.pem created in the Anjay-zephyr-client/demo directory.
Configure the Client#
-
Provide the generated certificate and private key through the shell in the serial communication program.
Note
Before setting configurations in Anjay you need to stop running Anjay by
anjay stopcommand.Run these commands and paste the content of the files generated in the previous step.
anjay config set public_cert anjay config set private_key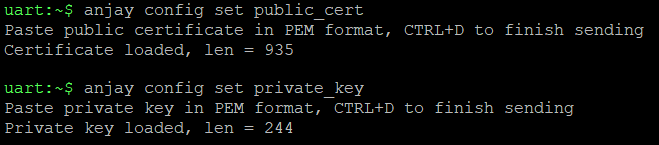
-
Save changes, start Anjay using
anjay startcommand and go to the next step to add a device to Coiote IoT DM.
Add device to Coiote IoT DM#
-
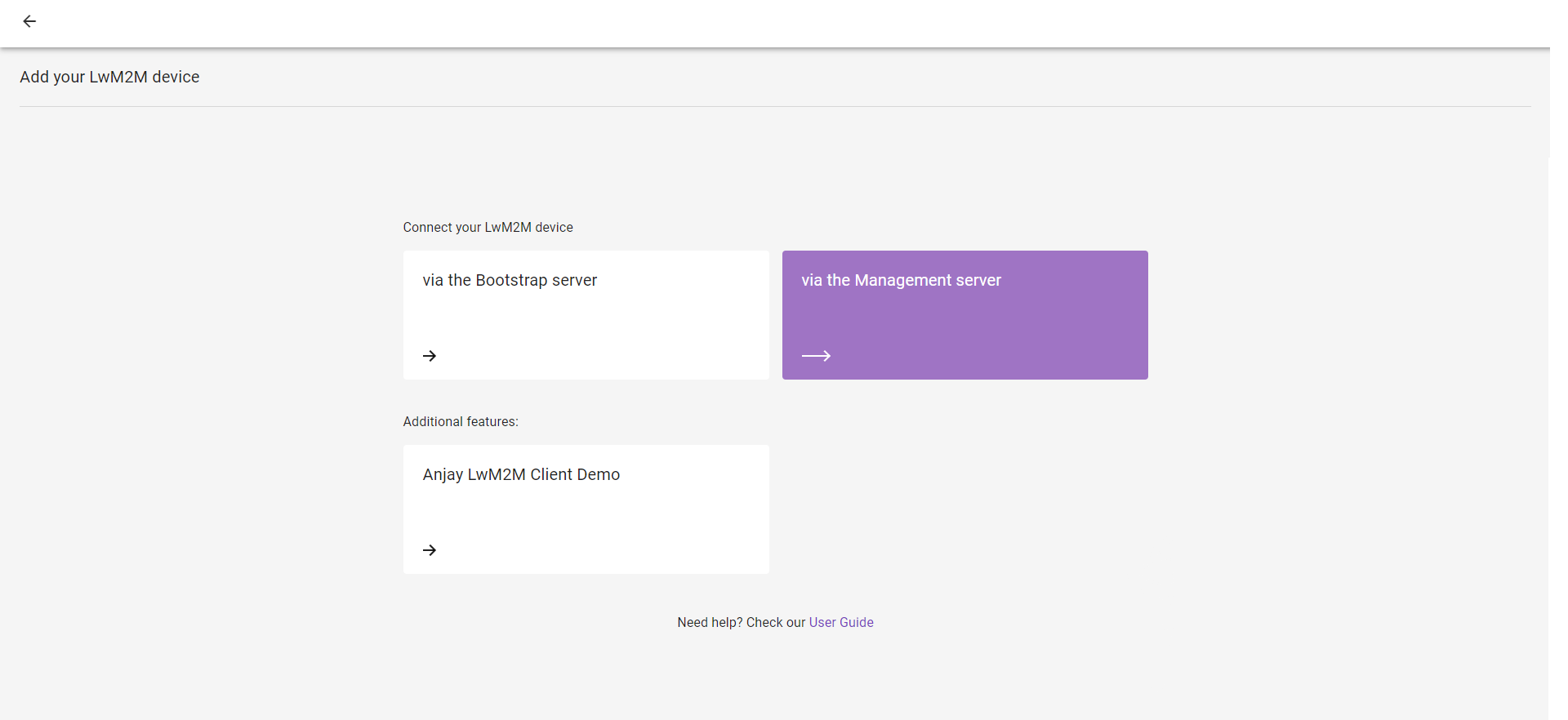
Upon logging in to Coiote IoT DM for the first time, you will see the Add your LwM2M device panel.
Note
If you had previously added a device, in Device inventory, click the Add device button.
-
Select the Connect your LwM2M device directly via the Management server tile.
- In the Device credentials step:
- In the Endpoint name enter your LwM2M device endpoint name, e.g.
anjay-zephyr-demo. - In the Security mode section, select Certificate mode.
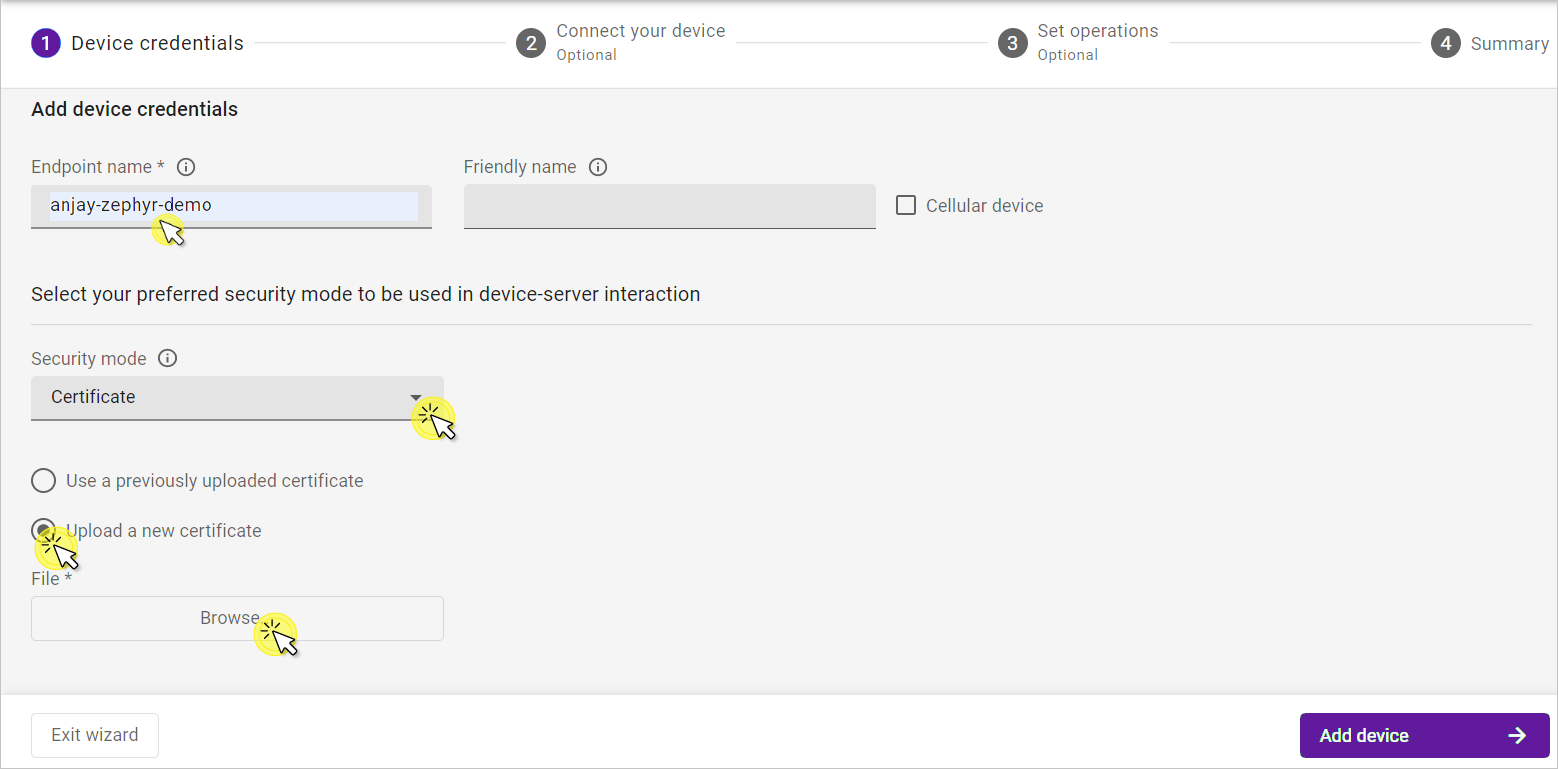
- Click Upload a new certificate and Browse.
- In the pop-up, go to the directory where your certificate has been generated, select the
cert.pemfile and click Open. - Click Add device.
- In the Endpoint name enter your LwM2M device endpoint name, e.g.
Note
The Endpoint name which you enter to the Coiote IoT DM should be the same as it is in the Client configuration.
- Click Next, Go to Summary to skip the third step, and Finish to see your Device Center.